n February 2023, ESET researchers detected a spearphishing campaign targeting a governmental entity in Guyana. While we haven’t been able to link the campaign, which we named Operation Jacana, to any specific APT group, we believe with medium confidence that a China-aligned threat group is behind this incident.
In the attack, the operators used a previously undocumented C++ backdoor that can exfiltrate files, manipulate Windows registry keys, execute CMD commands, and more. We named the backdoor DinodasRAT based on the victim identifier it sends to its C&C: the string always begins with Din, which reminded us of the hobbit Dinodas from the Lord of the Rings.
Key points of this blogpost:
- Operation Jacana is a targeted cyberespionage campaign against a Guyanese governmental entity.
- After the initial compromise via spearphishing emails, the attackers proceeded to move laterally through the victim’s internal network.
- To extract sensitive data, the operators used a previously undocumented backdoor we named DinodasRAT.
- DinodasRAT encrypts the information it sends to the C&C using the Tiny Encryption Algorithm (TEA).
- Apart from DinodasRAT, the attackers also deployed Korplug, leading us to suspect that China-aligned operators are behind this operation.
This campaign was targeted, as the threat actors crafted their emails specifically to entice their chosen victim organization. After successfully compromising the first couple of machines with DinodasRAT, the operators proceeded to move laterally and breach the target’s internal network, where they again deployed the DinodasRAT backdoor, along with additional malicious tools, among them a variant of Korplug (aka PlugX). The overview of the compromise flow in Operation Jacana is shown in Figure 1.
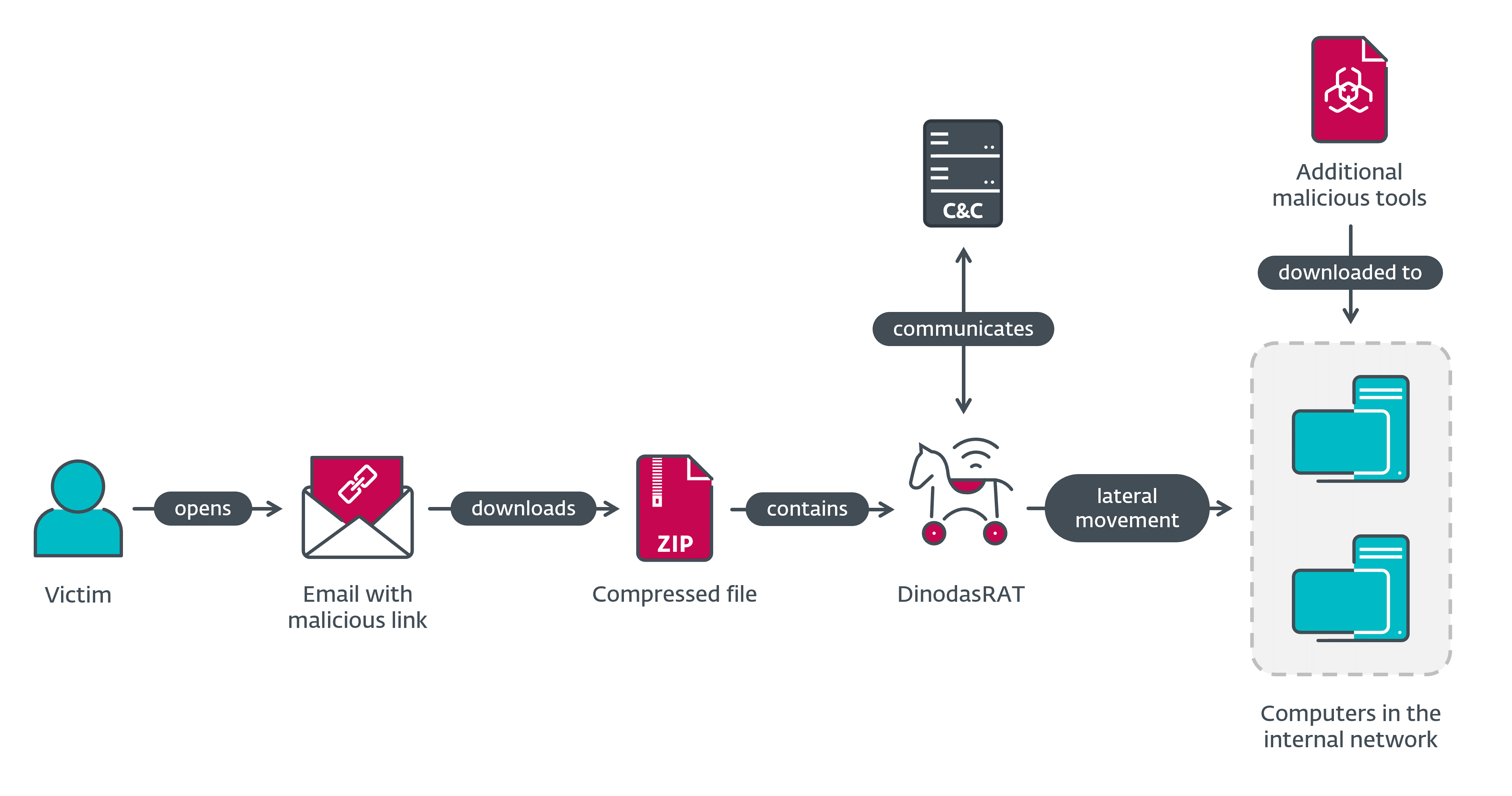
Attribution
As of this writing, we have not been able to attribute Operation Jacana to any known group. However, thanks to a clue we found, we feel that we aren’t completely in the dark regarding the perpetrators. During the attack, the threat actors deployed a variant of Korplug (aka PlugX), which is common to China-aligned groups – for example, Mustang Panda’s Hodur: Old tricks, new Korplug variant.
While our attribution to a China-aligned threat actor is made with only medium confidence, the hypothesis is further supported by recent developments in Guyana–China diplomatic relations. In February 2023, the same month that Operation Jacana occurred, the Special Organised Crime Unit (SOCU) of Guyana arrested three people in a money laundering investigation involving Chinese companies, an act disputed by the local Chinese embassy. Additionally, as part of the Belt and Road Initiative, China has economic interests in Guyana.
